As a security conscious partner to my clients, I get a lot of questions on cyber-security, and what to do to be "totally secure". Whilst it is impossible to be "totally secure", there are a number of simple steps you can take (and some that require a bit more configuration).

1. Realise that the weakest link in your security chain is 30 cm removed from the screen
All steps after this are moot if you are not vigilant. We can mitigate the consequences of an "Oops, oh no" moment - we can even reduce the probability of it happening, but we cannot take it away in its entirety. There is a constant "battle" between secure on one end of the spectrum, and usability on the other. Too much security exists - as it renders your system unusable. To little security and you are trying to keep out the mosquito with a barred gate. Simple things, such as locking your computer when you are not using it (no unlocked desktops that can be used by anyone passing your desk).
As such, in this article, the various security measures are rated with regards to a usability impact. The higher the impact, the more obtrusive it is to the user (and the more likely they will find a way to circumvent the security measure).
2. Authentication management
Prior to Two Factor Authentication (TFA - sometimes also referred to as MFA or Multi-Factor Authentication), username and password were the only measure of "secure" authentication. Some of the implemented practices caused "pseudo-security" - such as mandating complex passwords with an expiry date. It sounds secure - a password that is not a dictionary word, and had to be renewed to a new non-dictionary password every 30, 72, 0r 90 days. What happens in practice? The user notes down the password in a text-file, a notebook - I have even seen passwords written on a yellow sticky-note attached to the monitor. More inventive users come up with a password generation mechanism, which could be based on the month and year with some cleverly placed special characters. For example, if your password is renewed in August 2022, then you could device a password with this as a base - for example !AugPWD2022 - since there is a system for the user to follow, it is not likely to be written down. Of course, if an unauthorised person somehow finds out the system (which is not that difficult to do if you get hold of one password - subsequent passwords can be deduced), changing passwords with the same mechanism is useless.
The recommendation is to use a secure password manager, in combination with TFA. If your TFA provider supports passwordless sign-in, you should enable this. Zoho Vault can be configured in such way that when you log on with an unauthenticated device, after your user name (which is your email address), you are presented with a QR code to scan with Zoho OneAuth on your phone to authenticate (the phone must be unlocked by you, and you can even configure a secondary security barrier in Zoho OneAuth to authenticate you prior to scanning).
A well implemented Authentication Management system can be even less obtrusive than the traditional "username - password" authentication. But do it wrong (i.e. manually entered One-Time-Passcode via SMS or Authenticator app), and you will increase user frustration. Where possible, go passwordless.
3. Password management
Not every application you use in the business is capable of logging in without a password. In addition, there are applications for which you need to share the login details with other people. An enterprise password manager (don't let the word "enterprise" fool you - it is applicable to any size business) will be your secure way of storing, accessing, and sharing login credentials. A good password manager can even handle TFA sharing.
Zoho Vault is such password manager. And because of the extra sensitivity of the data - there is an extra step of a Vault Passphrase to access it - to access Zoho Vault, you must first authenticate your Zoho Account (preferably via Zoho OneAuth), and then each time you access Zoho Vault, enter a passprase (this is a longer phrase that only you know). Once logged in, you can access your passwords (single click login to supported applications and sites), and passwords for applications that are shared with you. Zoho Vault can also generate the One-Time-Passcodes required for TFA enabled login. ..
A good password management tool, with the appropriate business sharing process, increases both ease of use as well as security.
4. Device management
Pending on the size of your business, you may or may not consider a Device Management solution. In a small business environment, this usually leads to more "IT management overhead" than the actual security gains it provides. However, with more devices entering your organisation, it may be something to consider.
Before going the full Device Management as a software solution route - there are some simple steps to follow to increase the security of the devices used in your organisation to be considered as a policy.
First, it is highly recommended to encrypt the storage in any device that may have sensitive data installed on it. It is remarkably easy to access data on a computer if it is not encrypted. No hacking required - simply access the drive via a rescue OS - or mount the drive into a separate computer. No need for the user's credentials. Encrypting the drive makes that impossible without a decryption key.
Second, where practical, do not use bio-metrics to authenticate. A passcode is much more difficult to enforce than a "face scan" or fingerprint.
Third - always have an active firewall on the local device, blocking incoming traffic by default. Avoid using public networks.
Fourth - ensure the system is up to date. Patches are regularly released that "plug" holes in system security.
Fifth - as a user, trust nothing - if you receive an email, do not load remote images, click links, or open files if you do not know the origin of the message.
A device management policy will affect the perceived usability, because we are making it less easy/convenient to authenticate.
5. Secure your email server
You can reduce the dependency on the individual user to always do the right thing with emails, by limiting the number of malicious emails entering the user's inbox in the first place. Set up spam and malware protection on your mail server with policies. A good email server has spam guarding capabilities - if not, you must consider a third-party spam-guard application. Zoho Mail has its own built in, and you can set your policies to move unauthenticated messages to spam, quarantine, or in some cases reject outright (reject - the server does not accept the message, and sends a rejection message to the sender), Zoho Mail is included in the Virus Bulletin VBSpam Comparison - a unique position as the other entries are not mail servers, but dedicated spam guard solutions.
You can err on the side of caution with email servers, where a lot of emails from your business partners that simply did not do the work to properly authenticate their messages (see this article) end up in quarantine. However, get the balance right, and your email users do not notice the security operating in the background.
6. Sensitive data
Consider all business data as potentially sensitive. Your client data, internal data, either as part of a database or as a document - format does not matter. When you have taken the appropriate steps as per above, you have taken appropriate steps to make it more difficult for an external, non-authorised person to gain access to your digital assets. For internal leaks, however, there is a different strategy.
Obviously - but not without saying - you should limit access to as needed. It is always better to add privilege if needed, as taking away privileges will inevitably result in complaints and debate.
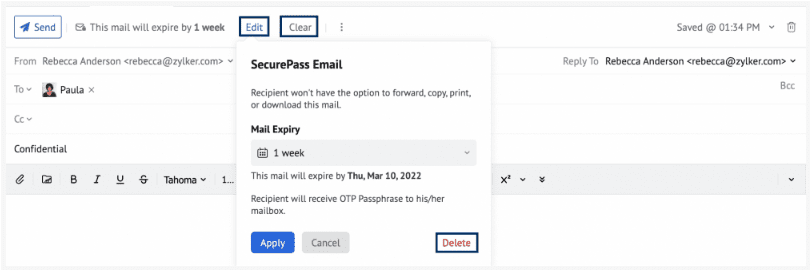
Sensitive emails, that should not be forwarded, should be protected - Zoho Mail does this via SecurePass email. The message is broken up into two parts. Part one lands into the inbox of the recipient - which contains a message that an email is waiting - clicking on the link, a One-Time-Passcode is sent to the same email address, which opens up the page on the web in which the message is located. Forwarding the original email will not provide the One-Time-Passcode to the forwarded recipient.
Should an employee leave the organisation, or if a device is lost, the ability to remotely disable access, and wipe the device is not a luxury. In Zoho One, we can remove the device from the trusted devices, and in WorkDrive immediately send a wipe instruction, removing all synchronised files and folders from the device.
The impact on the user will be: the more sensitive the data, the less "convenient" we make the access.
7. If you can't secure it (enough), monitor it!
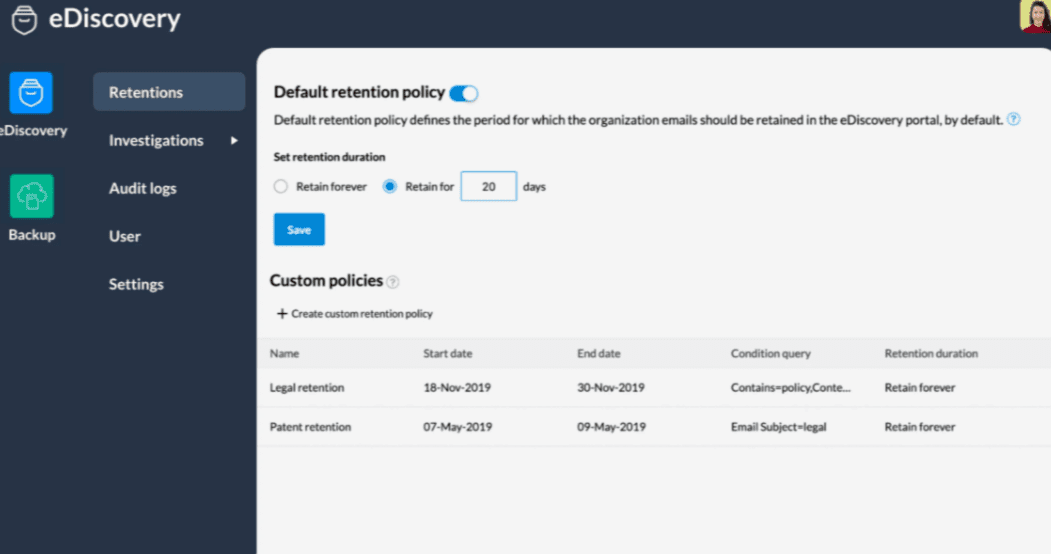
You cannot secure everything and expect a workable system. But it makes a big difference if you can audit access, and narrow down the "leak", if need be. And it certainly is a benefit if your employees are aware of this. With Zoho WorkDrive, a log is kept on who accessed what, and when. In addition, a in Zoho Mail, eDiscovery can be configured. This is an automated backup/replication tool that can be used to create legal hods, and is used for forensic analysis of emails. I know, it is difficult to imagine that OUR company would ever need this option - until it is that time you wished you had it.
Your users do not notice anything of this running in the background - and if they do not breach your policies with regards to sharing sensitive data, they will never notice this is running (other than in your organisation manual alluding to the fact that email communication on business systems may be monitored).
If you would like to upgrade your systems to a more secure environment, and discuss what the best balance is between security and usability in your particular situation, click the button below and contact us.
